Introduction
Nearly all businesses depend on the Internet today. Businesses need the Internet for communication, sales, operations, marketing, data storage, information processing, product development, customer service, and basically anything you can think of. The level of dependency on the Internet is such that if it came down, economic activity would come to a complete halt.
There is no business as usual without the Internet.
Even though the Internet is the world’s most powerful economic engine, representing huge growth opportunities, greater productivity, and access to new markets and audiences for businesses worldwide, it also poses many dangers. The sheer amount of activity on the Internet is an opportunity for cybercriminals looking to make big profits and, unfortunately, it is relatively easy for them to do so.
The Internet is a highly unregulated place and its enormous size and complexity means it can be abused and exploited in many different ways and most businesses and people are very vulnerable on multiple fronts. At Excedo, our mission is to help businesses understand how they are vulnerable so they can protect themselves and, by extension, the people that work for them, interact with them, and purchase from them. It is through understanding and proactive action that we can make the Internet safer for everyone.
Let’s look at the key areas businesses should be focusing on to stay safe from online threats and cybercriminals.
Email Security
Email is one of the main vectors for cyberattacks. Phishing, spam, spoofing, Account Takeover (ATO), Business Email Compromise (BEC), malware, Man-in-the-Middle (MitM), and Denial of Service (DoS) attacks all happen through email. These attacks take advantage of email’s inherent vulnerabilities and people’s general lack of security and risk awareness.
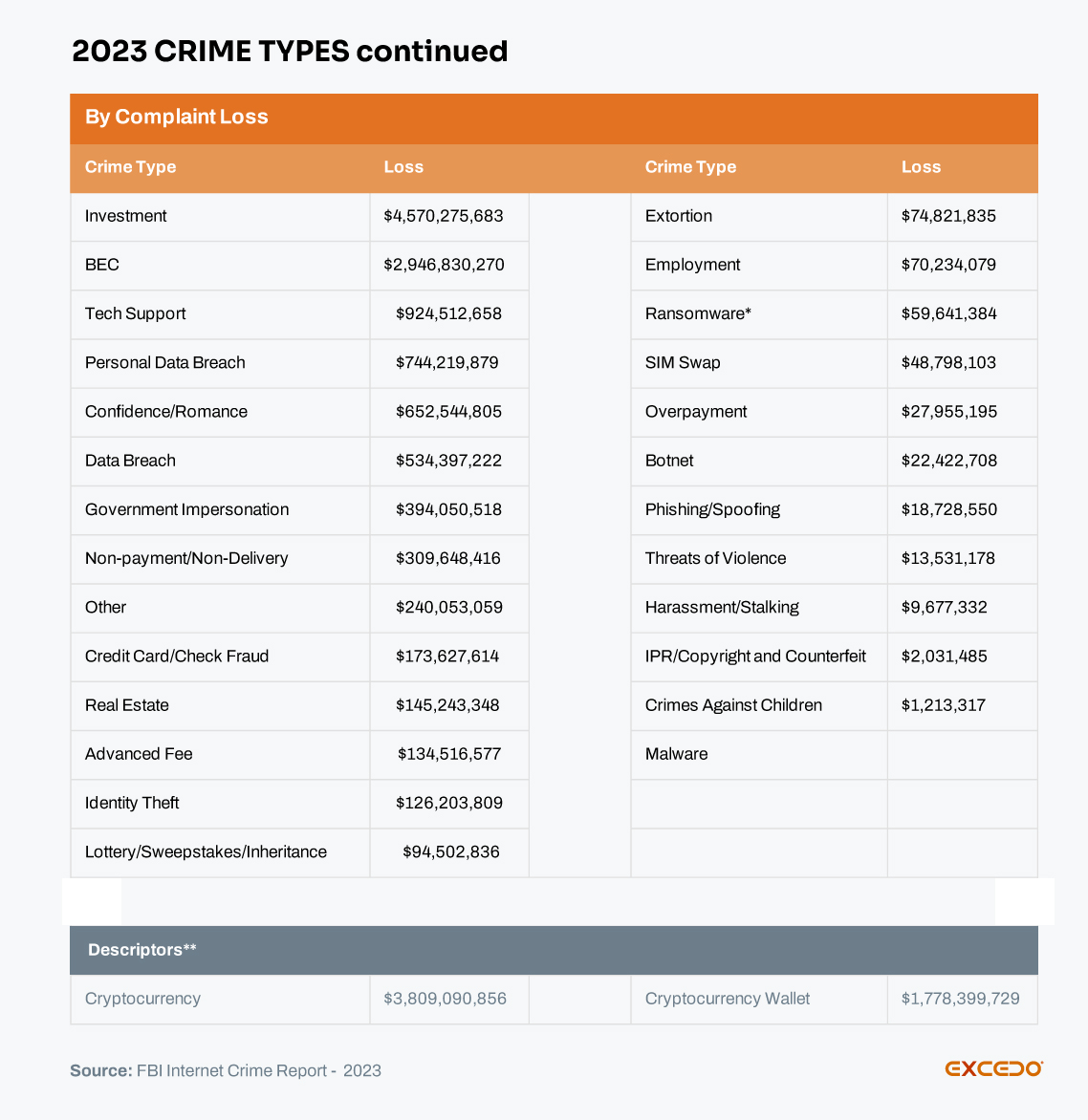
According to the FBI’s Internet Crime Complaint Center (IC3) latest annual report, malware, BEC and phishing/spoofing attacks alone led to over $3 billion in losses during 2023. However, the real number is likely much higher as this only accounts for reported cases and complaints.
Considering the scale and cost of email crime, email is not close to being sufficiently protected by default. In general, malicious and spam emails can reach people fairly easily without any red-flags or warnings being raised by the email system. At most, some emails end up in the spam folder, but they can still be opened and interacted with if one so wishes. It comes down to user discretion whether one opens or believes an email is legitimate.
This is a problem because most people do not have sufficient security training or knowledge to identify suspicious emails. Furthermore, fraudulent emails are becoming more sophisticated with the help of AI, making them far harder to spot.
For businesses to be safe on the email front, they need to implement measures that prevent malicious emails from reaching inboxes in the first place and that can warn recipients of potential danger. We recommend implementing the following:
DMARC Policy
One of the best ways to protect email is to properly implement a Domain-based Message Authentication, Reporting and Conformance (DMARC) policy.
A DMARC policy ensures only authenticated emails can reach your inbox and can be sent on behalf of your organization. Furthermore, it also informs recipients about how they should handle emails that fail authentication checks.
The DMARC policy can instruct recipients to:
-
"Quarantine" or "Reject" emails that fail authentication checks, meaning they should be sent to the recipient's spam or junk folder, or rejected outright.
-
"Monitor" emails that fail authentication checks, meaning receivers should send aggregate and/or forensic reports to the sender about the failed messages without taking immediate action.
Overall, DMARC helps you protect your email domains from unauthorized use and can prevent email spoofing and phishing attacks by allowing you to authenticate outgoing and incoming messages.
Anti-Malware and Anti-Spam Filters
Another important way to protect email is to install anti-malware and anti-spam filters.
Anti-malware and anti-spam filters analyze email attachments, links, and content for signs of malware, phishing, and other malicious activity. These filters will detect and block malicious content and unsolicited emails (spam) before they reach any inbox, thereby preventing your employees from being exposed to danger and fraud.
There are other measures that are necessary for email safety, but these will take you very far when it comes to protecting your email from different threats. With a DMARC policy, anti-malware, and anti-spam filters you will have a secure foundation upon which to build further security features, such as additional encryption, access control, and Data Loss Prevention (DLP) policies.
Web Security
Email is not the only way businesses are targeted online. Hackers and cybercriminals around the world are constantly scanning the Internet for vulnerable websites and web applications to target. Bot, Distributed Denial of Service (DDoS), SQL injection, cross-site scripting (XSS), file inclusion, and malware attacks all target websites.
Although the actual number is very difficult to know, research from the Open Worldwide Application Security Project (OWASP) suggests that over 30,000 websites are hacked every day globally. This represents a concerning level of vulnerability and indicates just how important it is for businesses to protect themselves on this front. Businesses should start by ensuring their websites and web applications have the following:
-
Correct HTTPS configuration
-
HTTP Strict Transport Security (HSTS)
-
Content Security Policy (CSP)
-
Transport Layer Security (TLS)
-
Up-to-date Digital Certificates
All of these ensure that your website connection is properly encrypted so external parties cannot inject malicious content, redirect pages, or steal information. The easiest way to find out whether your website has all of these enabled is to have it audited. You can contact us for a free Web Security Assessment here.
Beyond ensuring that websites and web applications are properly encrypted and have a private connection, we also recommend implementing the following:
WAF
A Web Application Firewall (WAF) protects web applications by filtering and monitoring all HTTP/S traffic between a web application and the Internet. A WAF can identify dangerous activity patterns, suspicious payloads, and vulnerabilities to instantly block and drop malicious traffic, such as bot traffic, before it can cause any damage or service interruptions.
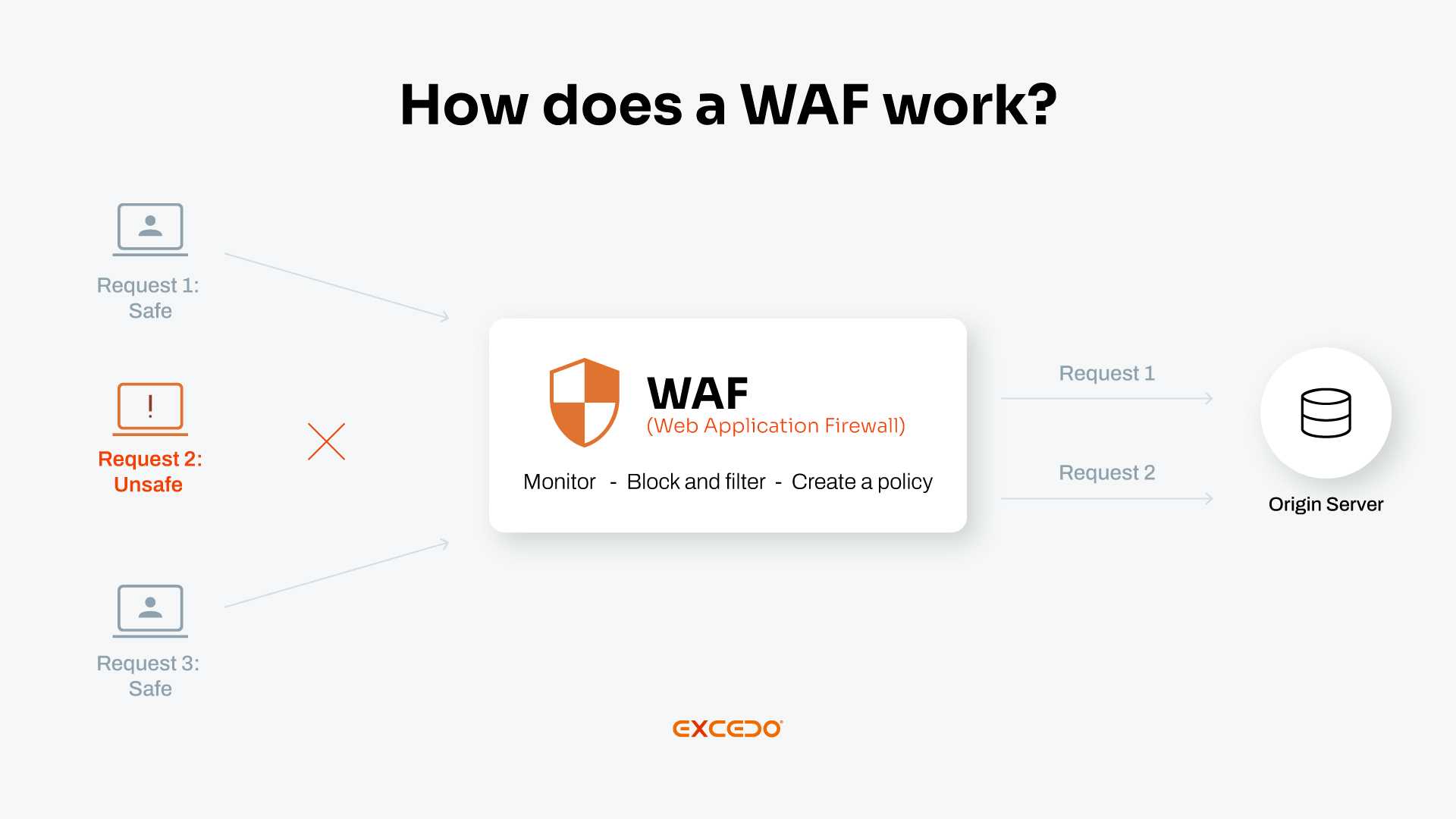
A WAF also ensures your web applications remain safe as threats evolve and change. WAFs use machine learning algorithms to learn new attack patterns and automatically update security policies to block new dangers, removing the need for time-consuming manual policy tuning.
DNS Security
Beyond email and websites, a third area of major online vulnerability for businesses is the Domain Name System (DNS). The DNS is basically a translation service which converts domain names to IP addresses that browsers can use to load Internet resources. It was never designed for security and DNS queries travel over the Internet in plaintext, meaning queries are unencrypted and anyone can intercept them - a vulnerability cybercriminals exploit frequently to launch DNS-based malware, phishing, ransomware, and DDoS attacks.
According to the International Data Corporation (IDC) 2023 Global DNS Threat Report which surveyed more than 1000 organizations across the world, over 90% suffered one or more DNS attacks in 2023, with an average cost of $1.1 million per attack. Additionally, nearly 50% of attacks led to application or service downtime and 30% resulted in data loss.
Most businesses already have some kind of DNS security in place, but clearly more needs to be done to keep customers and data safe. To increase your DNS security, we recommend implementing the following:
DNSSEC
A very basic DNS security measure that all businesses should activate is DNSSEC.
Without DNSSEC, the DNS will respond to any query and resolve any address requested of it - this is what it was designed for after all - without checking whether it is the authentic or authoritative one. DNSSEC is a security protocol that prevents this from happening by adding cryptographic signatures to responses from DNS servers. These signatures allow users to verify whether a DNS record comes from the authoritative name server (i.e. from you) and not from a rogue server impersonating you, thereby preventing common DNS attacks like domain spoofing and hijacking from taking place.
DNS Redundancy
Another common vulnerability of the DNS is that businesses' online resources will often rely on a single DNS server. This means if that server goes down or is overloaded, due to a surge in traffic as in a DoS attack for instance, all the resources and services that depend on it will go down too. A huge part of DNS security is therefore to implement structural redundancy by ensuring all online resources have multiple independent name servers, as in an Anycast routing system.
With Anycast DNS, traffic can be distributed (load-balanced) amongst multiple servers to make it much more difficult for a single server to be overloaded with queries. Additionally, even if one server does go down, others can take over, ensuring there is service continuity while the issue is resolved.
DNS Threat Intelligence
Aside from implementing DNSSEC and ensuring you have DNS or server redundancy, you should also make use of DNS threat intelligence to ensure you stay ahead of threats and attackers.
DNS threat intelligence provides full visibility over network traffic and activity to help you detect suspicious activity as it happens and before it can cause any harm. This empowers you to identify surges in traffic early, for instance, as well as whether they come from a suspicious source, so you can stop servers from being overloaded in the first place.
Conclusion
As we have seen, every aspect of online security, whether it is at the email, website, or DNS level, requires a holistic approach that considers multiple attack fronts and defence solutions. There is no silver bullet when it comes to making the Internet safer for businesses and people. Threats can come from any direction and at any level, so security must be multi-faceted and multi-layered too, making staying safe online a complex and constantly evolving process.
At Excedo, we try to make this process as simple and accessible as possible. We bring all the best solutions from leading technology companies together, so you don’t have to spend time combing through an infinite number of options and can start protecting yourself on all the necessary fronts from day one.




